Secure Internet Gateway
WHAT IS SECURE INTERNET GATEWAY?
Secure Internet Gateway is where you place your network inside a secure perimeter, providing robust, defence-level protection from ransomware, phishing, malware, and DDOS, among other modern IT security threats. Achieve complete compliance with security regulation and internet usage policies.
WHY USE SECURE INTERNET GATEWAY?
We have seen growing unprecedented breaches in the business environment. These breaches and security failures are very serious indeed for all organisations. This experience ends in costly downtime, resulting in vast amounts of lost revenue, while their reputation also suffers. This is before the costs of rebuilding the process are factored. The expenses associated with repairing the damage, improving security protocols, and redeveloping credibility with customers, are huge. Many businesses never recover.
The core advantages of the Secure Internet Gateway
Secure Connectivity
- Robust, high-security internet access conceived, designed, and built according to the ASD's rigorous requirements
- IRAP-assessed and certified by the ASD
- Approved as a defence-level security solution
- Supported 24/7 by the Vault Secure Operations Centre
Backed up with a self-service support portal for swift changes to configuration - Available across three different service levels
- Designed to be scalable, growing alongside businesses and other organisations
- Available as a standalone product, or as part of a Vault cloud subscription
- Can be deployed in multi-cloud or hybrid cloud environments
- Competitively priced — the highest-grade protection on a pay schedule that suits your organisation
- Flexible deployment options designed to meet varying security standards
- Secure internet access, designed according to the ASD Information Security Manual and ASD-Certified at Protected level
A scalable gateway that offers high performance and high security
Defence-standard secure gateway
Australia's defence industry, as well as the government agencies that oversee defence, are bound by the strictest regulations and protocols when it comes to cyber security. We developed the Vault SIG solution to meet these stringent requirements, giving our clients and partners in these fields peace of mind that comes from working with the very best.
We also strive to make this level of security a standard measure for all businesses and organisations. We believe that you should be able to leverage the very best from the digital landscape, and this means conducting your operations with complete confidence and security.
Built with scalability and growth in mind
Rigid solutions that work today but are untested in tomorrow's landscape are simply no good. With this in mind, the Vault SIG is designed to provide performance and security even at scale, growing alongside your business and remaining supremely effective.
You won't find operations and connectivity slowed down by excess functionality in your earlier stages of development. Nor will you find the gateway falling short when you need it most. Instead, you'll have the protection and performance you need, perfectly suited to the size, scale, and set-up of your operation.
A range of deployment options
Users can opt for our standalone Vault SIG solution, or they can use the gateway as part of the cloud subscription from Vault. You will also have the option to choose from multi-cloud or hybrid cloud architecture deployment.
In addition, there are three service levels available. Our basic service level still provides the defence-grade security you expect, but our higher tiers go beyond this.
Support designed to suit all users
The SIG is supported by Vault's 24/7 Secure Operations Centre, providing the expert assistance and guidance that users need. This is also supported by our self-service portal and resources designed to help users gain the best possible experience.
Our solution provides security event logging, auditing, and reporting give you and your organisation the insight you need into how your security protocols are performing. Meanwhile, the self-service support portal facilitates swift changes to managed firewalls.
ASD-certified, IRAP-assessed & 100% Australian-owned operated
You need to be able to trust your secure gateway. Vault's SIG has been assessed to Secret-level by IRAP and certified as Protected by ASD. All of Vault's cloud and security offerings are built according to strict ASD requirements for extra robust levels of security.
To back this up, we are 100% owned, operated, and legislated within Australia.
Priced with growth and availability in mind
We don't think that defence-level security should come with a premium price tag. A more secure, responsible approach to internet use benefits all of us here in Australia, right across our society, which is why we aim to make our solution available to all who need it.
This means competitive pricing, no additional or hidden fees for firewall changes or DDoS protection, and a range of different service level options to suit all budgets and user requirements.
How does it work?
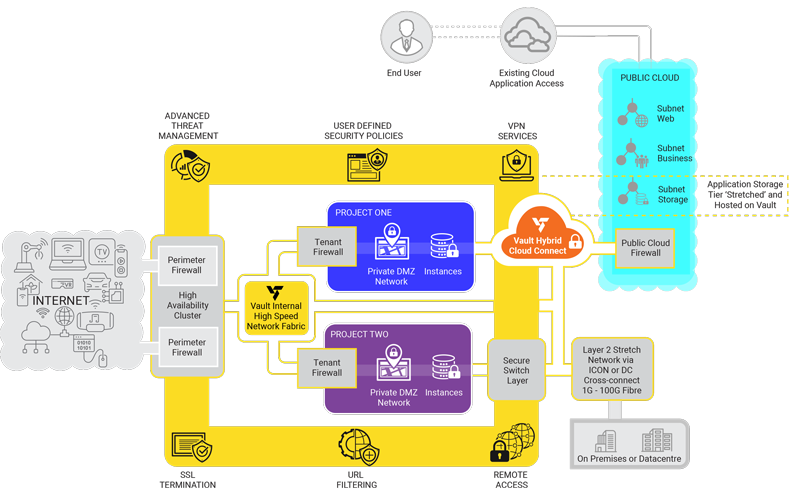
Typical use scenarios
Remote collaboration across flexible teams
Remote flexibility and capability are becoming increasingly important to organisations and configurations. This is only effective if you can rely on the security and performance of your connection, supporting flexibility in the field.
Supporting user login and activity
Users and customers expect round-the-clock support and availability, which means you may need to provide login portals and areas for your users. These need to be secured at a high level.
Setting access tiers for employees, partners and contractors
As your organisation grows, you are going to have different employees and partners with different access privileges. Add contractors to this mix, and the need becomes even more acute. The Secure Internet Gateway provides this tiered access.
Meeting the evolving rules, regulations, and legislation regarding data usage
Any organisation that handles personal data from users, customers, or any group is bound by strict regulation. What's more, this regulation is evolving alongside developing threats. Vault's SIG is designed with these regulations in mind, as is a certified IT security solution.
Developing products and operations in complete secrecy
Apply the highest levels of secrecy to product development, and require the highest tier of access credentials from any users accessing sensitive data and information.
Building trust and authority across user & client bases
Cyber security is a big deal these days, not just in the sphere of Australian IT but right across our society. Users, customers, clients, partners — all of these groups need to be able to trust the organisations they work with, and they value this trust very highly. Deploying the Vault SIG solution will help you build this trust.
Contact
General enquiries
For general queries, including partnership opportunities, please email hello@vaultcloud.com.au
Canberra
Level 5, West Tower
2 Constitution Avenue,
Canberra ACT, 2601
Sydney
Suite 2.119, Level 2
477 Pitt St,
Haymarket NSW 2000
Our Cloud Solution Architects are standing by to offer a free solution overview and quote based on your specific requirements.
Call our team on (02) 5110 9999
